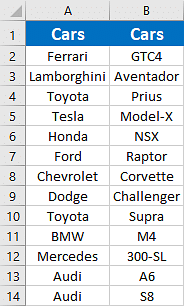
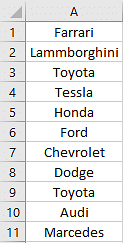
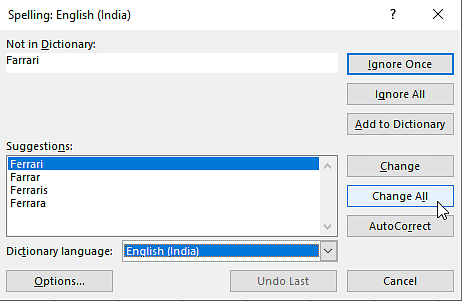
Life is a journey filled with unique experiences, challenges, and triumphs. Each of us walks a path that is distinctly our own, shaped by our personal stories and encounters. This individuality is what makes us who we are, and it’s why the advice we give and receive should always be taken with a grain of salt, especially when it comes from someone who hasn’t walked in our shoes.
"Don't let anyone who has not been in your shoes tell you how to tie them."
This phrase encapsulates a powerful truth about the value of personal experience. Let's delve deeper into why it’s crucial to trust your own journey and be cautious of unsolicited advice from those who haven’t lived through your struggles.
The Value of Personal Experience
Understanding the Depth of Challenges
Only you truly know the extent of the challenges you've faced. External observers might see the outcomes but often miss the nuances and complexities that led to them. For instance, overcoming a difficult period in your life or dealing with personal loss involves emotional and psychological battles that are invisible to others.
Building Resilience and Wisdom
Each challenge you encounter and overcome adds to your resilience and wisdom. These experiences teach you invaluable lessons that shape your decision-making process. When someone who hasn’t faced similar challenges tries to advise you, they lack the context and depth of understanding necessary to provide meaningful guidance.
The Dangers of Misguided Advice
Lack of Empathy
Advice from someone who hasn’t been in your shoes can often lack empathy. They might not grasp the emotional toll or the practical difficulties you’ve navigated. As a result, their suggestions may come across as insensitive or unrealistic.
One-Size-Fits-All Solutions
Life is not a one-size-fits-all scenario. What works for one person might not work for another. People who haven’t experienced your specific challenges might offer solutions that seem logical on the surface but fail to address the unique aspects of your situation.
Trusting Your Own Journey
Embrace Your Story
Your story is yours alone. Embrace it, with all its highs and lows, because it is what makes you unique. Trust in your ability to navigate through life’s challenges using the knowledge and strength you’ve gained from your own experiences.
Seek Advice from Those Who Understand
When seeking advice, turn to those who have faced similar challenges. Their insights are more likely to be relevant and practical. They understand the intricacies of your journey and can offer empathy along with guidance.
Cultivate Self-Confidence
Believe in your own ability to make decisions. You are the expert in your own life, and your instincts are often more reliable than the well-meaning but uninformed advice of others.
Conclusion
In life, it's important to remember that while advice from others can be helpful, it’s ultimately your own experiences that shape the best path forward. Don’t let anyone who hasn’t walked in your shoes tell you how to tie them. Trust yourself, embrace your journey, and seek guidance from those who truly understand your struggles. Your path is uniquely yours, and only you hold the wisdom gained from every step you’ve taken.
Remember, the way you tie your shoes is just as unique as the journey you’ve walked.